|
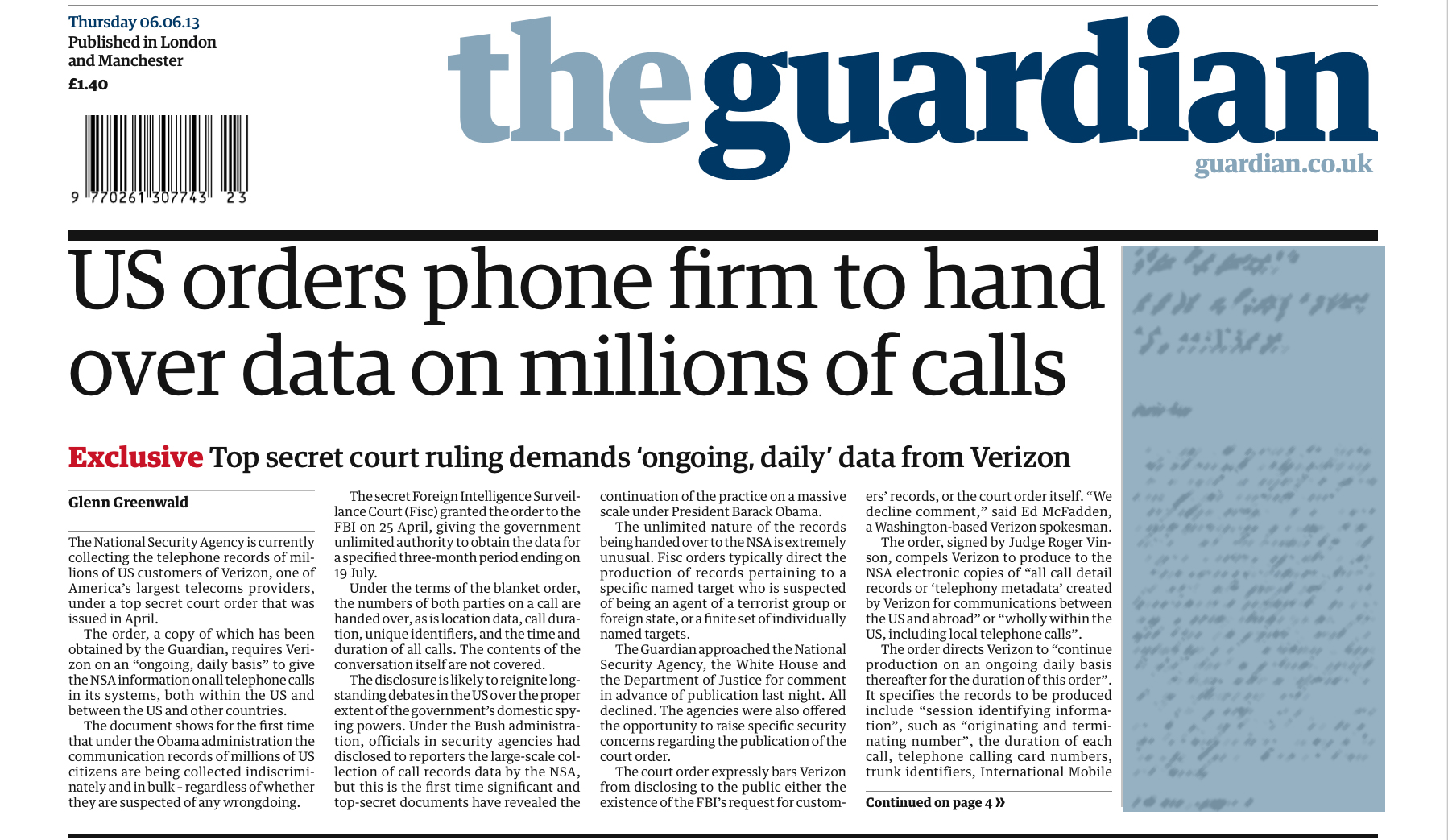
| Wichita Mid-Continent Airport |
Loewen, a 58-year-old avionics technician who worked at the airport for Hawker Beechcraft, was arrested before dawn as he tried to drive onto the tarmac. The materials in the car were inert, and no one at the airport was in any immediate danger, authorities said.
Loewen, who lives in Wichita, had been under investigation for about six months after making online statements about wanting to commit "violent jihad" against the United States, U.S. Attorney Barry Grissom said. An undercover FBI agent befriended Loewen, striking up conversations about terrorism and Loewen's admiration for those who plotted against American interests.
 |
| Wannbe Jihadist Terry Lee Loewen |
Loewen planned to die in the explosion, a fate that he said was inevitable in his quest to become a martyr in a "jihad against America", according to court documents.
"Since early summer, he was resolved to take an act of violent jihad against U.S.," Grissom said.
Authorities said "they believe" (But not Sure...?) Loewen acted alone. No other arrests were expected.
U.S. Attorney Barry Grissom at a statement about the alleged Plot
Loewen made an initial court appearance Friday afternoon, answering "yes" in a strong voice to procedural questions. A U.S. Court magistrate ordered that he remains jailed at least until a hearing next Friday after prosecutors said he was a flight risk and a danger to the community.
His wife and attorney declined comment after the hearing.
His brother-in-law, David Reddig, described Loewen as a "good guy". He said Loewen helped him pay off the debt on his truck and took care of his home and chickens (how cute...) after an eye injury kept him from working.
"He is a hard worker and all that stuff," Reddig said.
But he said also that Loewen kept details of his life away from his relatives and friends.
The case appears to be similar to a string of investigations conducted by the FBI since the
September 11th, 2001, attack. The FBI sting operations have prompted controversy over whether the law enforcement tactics involved entrapment of suspects and intruded on civil liberties. One involved an undercover agent who pretended to be a terrorist, provided a teenager with a phony car bomb, then watched him plant it in downtown Chicago.
But the FBI has argued that the stings are a vital law tool for averting potentially deadly terrorist attacks. And juries have returned tough sentences.
In Loewen's case, court documents allege that he talked about downloading documents about jihad, martyrdom and an al-Qaida "manual" during his online sessions.
Investigators said he also frequently expressed admiration for Anwar Al-Awlaki, the American-born al-Qaida leader who was killed in a 2011 drone strike in Yemen. Al-Awlaki emerged as an influential preacher among militants living in the West, with his English language Internet sermons calling for jihad, or holy war, or however you wanne call it, against the United States.
In August 2013, an undercover agent offered to introduce Loewen to someone who could help him engage in jihad. A few days later, he mentioned "providing a tour" of the airport for one of the undercover agents.
 |
| Anwar Al-Awlaki killed 2011 by drone strikes |
"Wow! That's some heavy stuff you just laid down. Am I interested? Yes, of course ! I still need time to think about it, but I can not imagine anything short of arrest stopping me," Loewen told the agent, adding that he needed to let Allah guide him.
The documents allege that he also asked for assurances that he wasn't being set up, saying his greatest fear was not completing the operation.
The criminal complaint also details a meeting in November 2013 with other undercover agents in which they discussed executing the plan before Christmas 2013 in order to cause the greatest damage and fear. He also provided components from his employer that the agents requested for wiring the fake explosive device, according to court documents.
Last Wednesday, Loewen met with another undercover agent and helped assemble the false bomb, court documents allege. Loewen was charged with attempting to use a weapon of mass destruction, attempting to damage property and attempting to provide support to terrorist group al-Qaida.
 |
| WOMD |
Loewen's neighbors said several law enforcement agencies converged early Friday morning at the modest brick home where Loewen and his wife live, just a few houses down from a local elementary school. Some neighbors said the couple mostly kept to themselves and didn't participate in neighborhood events.
Janine Hessman, who lives nearby, said she didn't know Loewen well but liked his wife and spoke to her often. But if the allegations are true, she said, "I don't really have any sympathy for him."
SOURCE: National Public Radio